Our information security risk management framework, information security policy, specific management plans, and resources allocated to information security management are as follows:
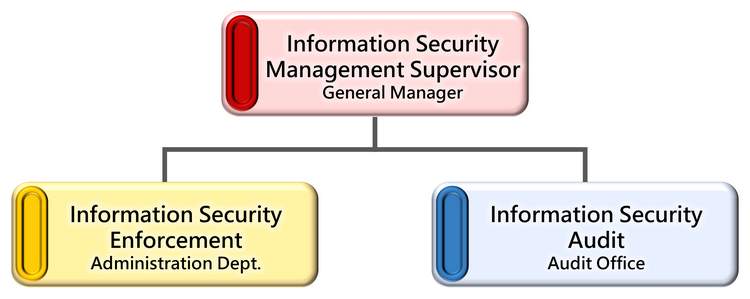
Organizational Structure
To strengthen the company's information security management and ensure data, system, and network security, the Management Department is mandated to have an Information Security Manager and an Information Security Officer responsible for implementing the information security system, including network and system management. We also continuously review and assess trends in the information environment, assess information security risks, and protect against them to ensure the continued effectiveness of our internal information security management mechanisms.
Information Security Audits oversee the implementation of internal information security. If any deficiencies are identified, the audited units will be required to propose relevant improvement plans and specific measures. Improvement results will be regularly and continuously tracked to reduce internal information security risks.
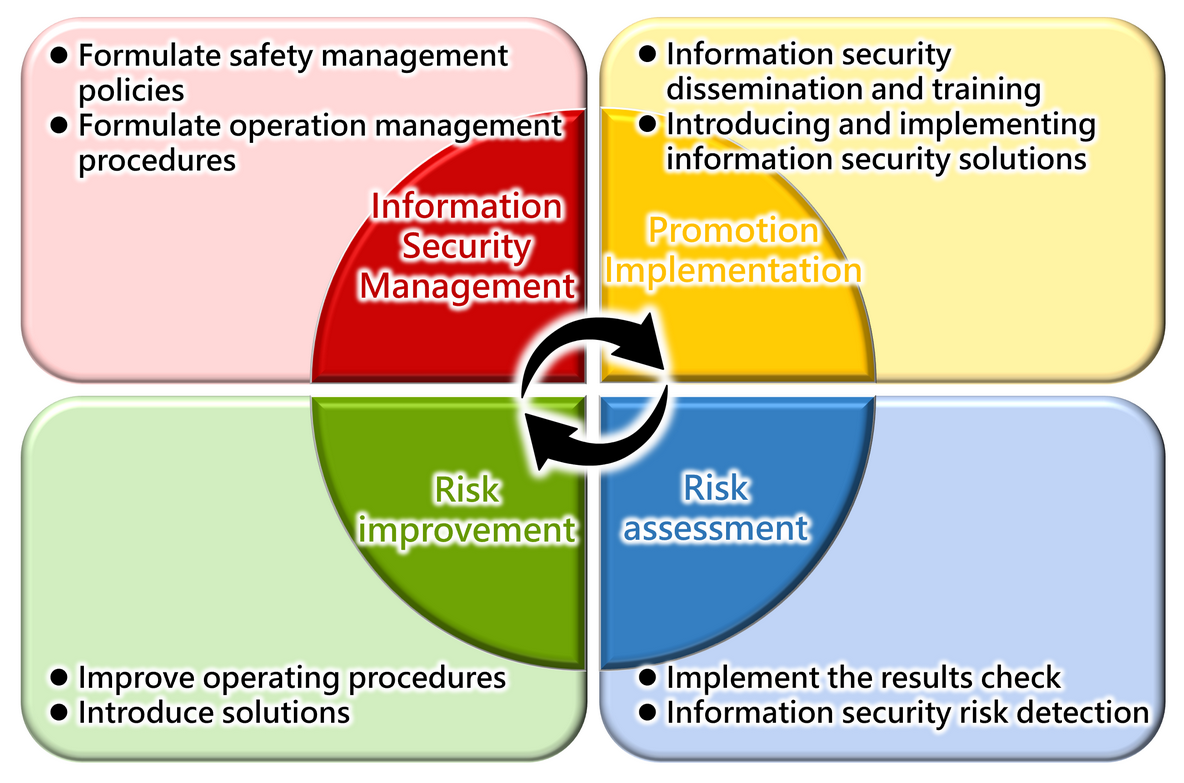
Information Security Operational Model
Information Security Policy
Information Security Objectives
Establish a secure and trustworthy computerized operating environment to ensure the confidentiality, integrity, and availability of the company's information assets (software, hardware, computer data, information environment, and personnel), protect against various internal and external threats, and ensure the sustainable operation of the company's information systems.
Information Security Scope
● Personnel management and information security education and training.
● Computer information system security management.
● Network security management.
● System access control.
● Information asset security management.
● Physical and environmental security management.
● Information security audits.
Information Security Principles and Standards
● Regularly conduct information security education, training, and promotion, including information security policies, legal requirements, information security operating procedures, and the proper use of IT facilities. This helps employees understand the importance of information security and various security risks, enhance employee information security awareness, and ensure compliance with information security regulations.
● To prevent information systems and files from being infected by computer viruses, proactive virus detection, proactive intrusion detection, and preventive measures are implemented for computer viruses, intrusions, and malicious attacks to ensure computer data security.
● To prevent natural disasters or major man-made events that could disrupt important information assets, critical business operations, or communication systems, information system recovery measures must be established.
Regulations Employees Must Comply with
● Management Department IT personnel shall create "user accounts" based on the information access request form.
● Computer data and equipment must not be arbitrarily destroyed, removed, loaned out, or improperly modified to maintain data integrity.
● The use of unlicensed or unauthorized software is prohibited.
● When completing work or when not in use for an extended period, the machine must be shut down to prevent confidential data from being leaked or compromised.
● Computer equipment should be stored away from tea, coffee, sunlight, or humid locations. The equipment should be kept clean and the wiring organized to extend its lifespan.
● Upon resignation or when a new position is handed over, Management Department IT personnel will assess the relevance of data and access rights and make appropriate arrangements.
● If computer equipment is not functioning properly, users must immediately notify Management Department IT personnel for inspection and repair.
Information Security Policy Revision
● The information security policy will be reviewed when there are significant changes or trends in the information environment.
● The information security policy will be reviewed annually to confirm that the relevant regulations meet requirements.
Specific Management Plan
Our company's information security management plan is as follows:
| Item | Management Plan |
|---|---|
| Firewall Protection | Firewall connection rules are set. Special connection requirements require additional application. Set a blacklist of websites to prohibit access to gaming websites. |
| Antivirus Software | Use antivirus software and automatically update virus signatures to reduce the chance of virus infection. |
| Email Security Control | Automatic email scanning and threat protection proactively prevent unsafe attachments, phishing emails, and spam, and extend protection against malicious links. Automatically back up every outgoing and incoming email. |
| Data Backup Mechanism | Daily backups are set for critical information systems, databases, and file servers. Backup data is stored offsite. |
| HR Security Management | Conduct regular information security awareness campaigns. |
| Information Security Incident Reporting |
Report incidents to the relevant authorities based on severity. Detailed records of incidents and data are kept for subsequent review and improvement. |
| File Upload Server | All important user files are stored on the server and centrally backed up and maintained by the management department. |